Maintenance and repair of computer. Control work for the CSC group in the discipline "maintenance and repair of computer systems and complexes". Application software
At the beginning of the internship, there was a safety briefing. After passing the briefing, familiarization with the activities this enterprise and the study of his work, as well as the consolidation and deepening of the knowledge gained during the training sessions.
Share work on social networks
If this work does not suit you, there is a list of similar works at the bottom of the page. You can also use the search button
Introduction………………………………………………………4
1. General information about the enterprise (history of creation, development and structure of the enterprise). ……………………………………………..5
2. Enterprise computer software. …………….7
3. Control of the technical condition of computer equipment and computer systems. …………………………………………….eight
4. Safety precautions at the enterprise. ………………………9
5. Approximate content of the practice. ……………………………..
5.1. Special programs used in the enterprise for diagnostics and maintenance of the operating system and equipment of a personal computer. ………………………………….
5.2. Maintenance and repair of computer systems and complexes. …….. 21
5.3. Applying repair skills computer equipment…. 22
Conclusion. ……………………………………………………………..26
Bibliography. ………………………………………………27
Appendix ………………………………………………..29
Change
Sheet
Document No.
Signature
the date
Sheet
PP.03
Developed
Vaseeva V.V
Check.
Mikhailov M.M.
N. Contr.
Mikhailov M.M.
Lit.
Sheets
GOU SPO "ZabGK im. M.I. Agoshkov"
Gr. KS-13-1(230113
INTRODUCTION
The production practice took place from June 22 to July 4 at the enterprise ZabGK named after M.I Agoshkov. The director of the enterprise is Zykov Nikolai Vasilyevich, the deputy director of the enterprise is Efimenko Tatyana Ivanovna, the head of the practice is Mikhailov Mikhailovich.
The purpose of the internship is:
Familiarization with the activities of the enterprise;
To consolidate theoretical knowledge on all issues of maintenance of computer equipment;
Show primary professional skills in maintenance of computer equipment and computer networks;
At the beginning of the internship, there was a safety briefing. After passing the briefing, they got acquainted with the activities of this enterprise and studied its work, as well as consolidating and deepening the knowledge gained during training sessions.
Computers and Information Technology intensively develop in the spheres of material production. Specialists different professions are increasingly using a computer in their workplace, as well as using information and communication technology in their professional activity.
Change
ist
Document No.
Signature
the date
Sheet
PP.03 Maintenance and repair of computer systems and complexes
- GENERAL INFORMATION ABOUT THE ENTERPRISE (HISTORY OF CREATION, DEVELOPMENT AND STRUCTURE OF THE ENTERPRISE)
The formation of the Trans-Baikal Mining College as an educational institution that trains specialists for mining industry originates in 1917. Far away, full of political events historical significance In 1917, when polytechnic courses were organized in the city of Chita with a mining department headed by mining engineer Banshchikov A.N. (“Zabaikalskaya Nov”, June 20, 1917).
- Since September 1917, it has become an independent mining department at the Polytechnic School. It was headed by mining engineer A.N. Banshchikov.
- In September 1947, the Polytechnic School received the status of a technical school and the name "Chita Mining College".
- In January 1994, the Chita Mining College, which was under the jurisdiction of Zabaikalzoloto JSC, was taken under the jurisdiction of the Ministry of Education of the Russian Federation.
- In August 1996, the Chita Mining College was under the jurisdiction of the Ministry of General and vocational education and is called - State educational institution secondary vocational education Chita Mining College.
- In September 1997, the Training and Course Combine (UCC) at the Chita Mining College resumed work for theoretical and practical training in professional training programs.
- In October 1998, the training and consulting center (UCP) in Krasnokamensk resumed its work to train mid-level specialists in correspondence courses at the PIMCU enterprise.
- In September 2002, a branch was created in Krasnokamensk on the basis of UKP.
- In September 2005, the Mining College became a college and acquired a new name Federal State Educational Institution of Secondary Vocational Education Zabaikalsky Mining College.
Change
Sheet
Document No.
Signature
the date
Sheet
PP.03 Maintenance and repair of computer systems and complexes
- In May 2009, by order of the Federal Agency for Education dated May 27, 2009 No. 544, the institution was renamed the Federal State Educational Institution of Secondary Vocational Education
Transbaikal Mining College named after M.I. Agoshkova
- In October 2012, he became the Laureate of the competition in the nomination "100 Best Colleges of Russia" (St. Petersburg 2012)
Change
Sheet
Document No.
Signature
the date
Sheet
PP.03 Maintenance and repair of computer systems and complexes
2. Enterprise computer software
During my internship, I worked with the computer labs of the college, in which there were from 10 computers for each classroom. When working with these computers, I studied their characteristics (which are given below). Basically, these computers are suitable for working in this area, since they mainly work with the standard Microsoft Office package (most often MSWord and MSExcel). And on these computers, programs for teaching computer literacy are used. Also, these computers do not have specialized or other software that does not meet the characteristics of this computer and does not require large resources.
Computer name: 302 - 1-9
Operating system: Microsoft Windows XP Professional SP 2 Language-Russian (standards: Russian)
Processor: IntelInsidePentium 4
Memory: 512 MBRAM
Version: DirectX DirectX 9.0
Current screen mode: 1024x768 (32bit)
Brand : LG Disk 3.5(A:) Yes
Disk (D:): For CD-RW
Disk Capacity: (C:) 80 GB
Videos card : VGA Tech Graphics. Controller
Keyboard Standard keyboard: 101/102
Brand: Genius Mouse Optical NTFS File System
Change
Sheet
Document No.
Signature
the date
Sheet
PP.03 Maintenance and repair of computer systems and complexes
3. CONTROL OF THE TECHNICAL CONDITION OF COMPUTER EQUIPMENT AND COMPUTER SYSTEMS
Computer technology in the educational institution is in excellent condition.
All computers have been updated and replaced recently, many of them have been replaced with parts that greatly increased the performance of the PC. System administrators monitor the state of all equipment located in the Mining College. At the moment, many PCs do not require any investments. The technical condition of monitors, printers, system units, as well as other peripheral devices are under control. In the event of a breakdown of computer equipment, measures are immediately taken to eliminate all problems. If necessary, replace RAM, hard drives, motherboards, video cards, if these components cannot be repaired.
Technical condition of computer networks.
On the second floor, almost all classrooms have Internet access and are currently in excellent condition, which allows students and college staff to access the Internet without much difficulty. On the first, third and fourth floors there is also Internet, but partially. All cables are insulated and protected by special protective cases. If there is any breakdown in the network, it is eliminated without much effort. The main attention is paid only to software for convenient work on a PC.
Change
Sheet
Document No.
Signature
the date
Sheet
PP.03 Maintenance and repair of computer systems and complexes
4. SAFETY AT THE ENTERPRISE
Before you start repairing your computer, perform the following steps in the order listed:
1. Turn off your computer and all peripherals.
2. Before touching the inside of the computer, touch an unpainted metal surface on the computer chassis, such as the metal trim around the card slot opening on the back of the computer. During operation, periodically touch an unpainted metal surface of the computer case to remove static electricity which may damage internal components.
3. Unplug your computer and peripherals from electrical outlets. You should also disconnect your computer from all telephone lines and communication lines. This reduces the risk of injury or electric shock.
Also, always do following rules safety precautions:
When disconnecting a cable, pull it by the plug or by the special loop, but not by the cable itself. Some cable connectors are equipped with locking tabs: when disconnecting these cables, press the locking tabs before disconnecting the cable. When disconnecting the connectors, try to space them in a straight line so that the contacts do not bend. Also, make sure both connectors are correctly oriented and aligned with each other before connecting the cable.
Handle components and boards with care. Do not touch components or pins on the board. Hold the card by the edges or by the metal mounting plate. Hold electronic components, for example, the microprocessor by the edges, not by the contacts.
Caution: There is a danger of a new battery exploding if it is incorrectly installed. Replace the battery only with the same type or as recommended by the battery manufacturer. Dispose of used batteries according to the manufacturer's instructions.
Change
Sheet
Document No.
Signature
the date
Sheet
PP.03 Maintenance and repair of computer systems and complexes
5.PP.03. MAINTENANCE AND REPAIR OF COMPUTER SYSTEMS AND COMPLEXES
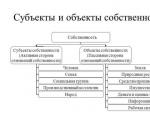
5.1 Special programs used at the enterprise for diagnostics and maintenance of the operating system and personal computer equipment.
Plan.
-
- basic software
- Operating Systems
- utility programs
- Applied software.
Under software(Software) is understood as a set of software and documentary tools for the creation and operation of data processing systems by means of computer technology. In the most general terms, computer software can be divided (depending on the purpose) into systemic, instrumental and applied (like any classification, this division is conditional).
Software is either data for use in other programs, or an algorithm implemented as a sequence of instructions for a processor.
Software called upon:
Ensure the performance of the computer;
Facilitate user interaction with the computer;
Expand the resources of the computing system;
Improve the efficiency of resource use;
Increase the productivity and quality of the user's work.
In computer jargon, the word " software » from English software , which was first applied in this sense in the American Mathematical Monthly paper by Princeton University mathematician John W. Tukey in 1958. In the field of computing and programming, software is the totality of all information, data, and programs that are processed by computer systems.
Change
Sheet
Document No.
Signature
the date
Sheet
51 0
PP.03 Maintenance and repair of computer systems and complexes
System software.
is a set of programs that provide effective management components of a computing system, such as a processor, RAM, input-output channels, network and communication equipment, etc.System softwareorganizes the process of information processing in a computer and provides a normal working environment for application programs; it is designed to control a computer, organize problem solving and user interaction with computer hardware. It is so closely related to the hardware that it is sometimes considered part of the computer. The richer the system software, the more productive the work on the computer becomes.
System software includes operating systems, service software (shells, utilities, anti-virus tools) and maintenance programs (test programs, control programs).
Basic software.
Basic software in computer architecture special position. On the one hand, it can be viewed as part hardware, on the other hand, it is one of the software modules operating system.
Operating system.
Operating system(OS) is a complex special programs nye tools designed to control the loading of a computer, the launch and execution of other user programs, as well as to plan and manage the computing resources of a personal computer. It provides control over the processing of information and interaction between the hardware and the user.
Operating system features include:
- dialogue with the user;
- input, output and data management;
- planning and organization of the program processing process;
- distribution of resources (RAM and ultra-fast memory, processor, external devices);
Change
Sheet
Document No.
Signature
the date
Sheet
52 1
PP.03 Maintenance and repair of computer systems and complexes
- launch programs for execution;
- all kinds of auxiliary maintenance operations;
- transfer of information between various internal devices;
- software support operation of peripheral devices.
The main need of the OS is that it hides complex unnecessary details of interaction with the hardware from the user, forming a layer between them.
One of the most important functions of the OS is the automation of the processes of input-output of information, the management of the execution of applied tasks solved by the user.
Based on the functions performed,OS can be divided into three groups: single-tasking (single-user), multi-tasking (multi-user) and networked.
Single-tasking OS are designed for the work of one user at any given moment with one specific task. Their appearance was stimulated by the creation of a large class of personal computers. An example of such an OS is the operating system MS DOS widely used until the early 1990s.
Multitasking OSprovide for the collective use of a PC in a multiprogram time-sharing mode, while the PC memory contains several task programs and the processor distributes computer resources between tasks. An example is operating systems. UNIX, OS/2, Microsoft Windows 95, Microsoft Windows 98, Microsoft Windows 2000, Microsoft Windows Me, Microsoft Windows XP.
Network OS associated with the advent of local and global networks and are designed to provide access to all computer network resources, such as operating systems Novell Net, Microsoft Windows NT, UNIX, IBM LAN.
Depending on the number of simultaneously processed tasks and the number of users,that can serve the OS, there are four main classes of OS:
Single user single task: support one keyboard and can only work with one (at the moment) task;
Single user single task with background printing, which allow, in addition to the main task, to run one additional one, focused on printing information. This speeds up the work when issuing large amounts of information for printing;
Change
Sheet
Document No.
Signature
the date
Sheet
54 2
PP.03 Maintenance and repair of computer systems and complexes
single user multitasking, which provide one user with parallel processing of several tasks;
multi-user multi-taskingallow several users to run multiple tasks on the same computer. These operating systems are very complex and require significant machine resources.
To be complete, an OS must contain at least the following main components.
file system.
Drivers for external devices.
Command language processor.
One of the primary tasks of the operating system is toread disk drive management and access to it. It is no coincidence that early PC operating systems contained the abbreviation DOS (Disk Operating System ) in their name. For this, the file system is used. Any application program has access to the file system, for which all programming languages have special procedures. For a PC, the file system is, to a certain extent, the basis of system software.
Support for a wide range of external devices is one of the most important functions of the OS.
In modern operating systems, there is an intermediate level between application programs and hardware, a kind of buffer called API (application programming interface) application programming interface). API provides the programmer with the ability to call certain general-purpose procedures that access specific hardware resources. As new equipment becomes available, it is updated and API , however, this may not be enough.
Correct work with the hardware is provided by drivers. Drivers programs that expand the capabilities of the OS to manage input / output devices, RAM, etc. With the help of drivers, it is possible to connect new peripheral devices or non-standard equipment to the computer. Each type of external device has its own driver. Standard device drivers form a set of basic input / output system (BIOS), which is often stored in the ROM of the PC system unit.
Every OS has a command language that allows you to perform certain actions accessing a directory, launching application programs, etc. The analysis and execution of user commands is carried out by the OS command processor.
Change
Sheet
Document No.
Signature
the date
Sheet
55 3
PP.03 Maintenance and repair of computer systems and complexes
To communicate with the OS, a shell is often used this is what the user sees on the monitor screen when working with the system.In essence, this is a kind of application program that is loaded on top of the OS and implements a command language that serves to provide user access to system functions. The shell is just a kind of utility for entering information that provides convenient access to the operating system, but it is not part of the OS.
File management and job scheduling programsthese are ready-to-execute programs (files): utilities, programming systems, tool systems, integrated software packages, computer graphics systems, database management systems (DB), application packages and programs.
Communication programsprograms designed to organize the exchange of information between computers.
Testing, control and diagnostic programsare used to check the correct functioning of computer devices and to detect malfunctions during operation, indicate the cause and location of the malfunction.
Memory management programsprovide more flexible use of OP computers.
Print programsoutput information to the printer.
Service programs.
Other set of programs official . This is a set of software products that provide the user with Additional services in working with a computer and expanding the capabilities of operating systems.These are various service programs used when operating or maintaining a computer - editors, debuggers, diagnostic programs, archivers, anti-virus programs and other auxiliary programs. These programs make it easier for the user to interact with the computer. They are adjoined by programs that ensure the operation of computers on the network. They implement network protocols for the exchange of information between machines, work with distributed databases, teleprocessing of information.
Change
Sheet
Document No.
Signature
the date
Sheet
57 5
PP.03 Maintenance and repair of computer systems and complexes
Under maintenance programsrefers to a set of software and hardware tools for diagnosing and detecting errors in the operation of a computer or a computing system as a whole.They include diagnostic tools and test control of the correct operation of the PC and its individual parts,as well as special programs for diagnostics and control of the computing environment, which automatically check the system's performance. These programs are used to check the performance, adjustment and technical operation of computer equipment by the personnel who serve it. The results of the work of such programs are displayed in a visual form and can be useful to a user with a qualification not lower than a computer operator.
Utilities auxiliary programs, they expand and complement the corresponding capabilities of the operating system (OS)mainly for the maintenance of disks and the computer file system.
packers programs that allow you to write information on floppy disks in a denser form, that is, create smaller copies of files, as well as combine several files into one (archive).
Antivirus programsprograms designed to prevent infection with computer viruses and eliminate the consequences of infection.Antivirus protection softwareprovide diagnostics (detection) and treatment (neutralization) of viruses. The term "virus" refers to a program that can multiply, infiltrating other programs, while performing various undesirable actions.
Application softwaredirectly aimed at solving professional problems, reducing labor intensity and increasing the efficiency of the user in various areas of human activity. These programs allow you to almost completely automate the tasks solved by the user. The programs of this group are very diverse: from simple programs text information processing to powerful publishing systems; from solving simple computational problems to powerful professional systems of mathematical calculations, accounting programs.
Currently, hundreds of thousands of different application programs have been developed and are being used for various applications. The most widely used programs are:
Change
Sheet
Document No.
Signature
the date
Sheet
58 6
PP.03 Maintenance and repair of computer systems and complexes
- preparation of texts (documents) on a computer text editors;
- preparation of documents of typographical quality publishing systems;
- creating and editing images graphic editors;
- tabular data processing spreadsheets;
- processing of information arrays database management systems;
Text editorsand publishing systems provide the ability to prepare documents on a computer. Text editors (NotePad - developed by Microsoft) are capable of performing basic editing functions: typing, making corrections, saving, working with fragments. Word processors (Microsoft Word, - developed by Microsoft), in addition, have the possibility of a variety of design, and some allow you to create documents that are intended to be viewed not on paper, but on a computer ( electronic documents). Publishing systems automate the process of layout of printing publications. Publishing systems are distinguished by advanced controls for the interaction of text with page settings and graphic objects, but have weaker capabilities for automating text entry and editing. It is advisable to apply them to documents that are pre-processed in word processors and graphic editors.
Spreadsheetsprovide work with large tables of numbers.Main purposespreadsheets - processing of various types of data presented in tabular form, for example, planning and financial, accounting documents, small engineering calculations. The main advantage of spreadsheets, compared to word processors (where tables can also be maintained, small calculations and sorting can be done), is that the content of some cells can automatically change in accordance with the change in the content of others, in other words, formulas can be stored in the cells. In addition, spreadsheet editors have the ability to maintain small databases and visualize data in the form of various tables, charts and graphs, i.e. spreadsheet tools, tabular calculation tools are supported by the ability to create visual reports. They find wide application in accounting, analysis of financial and trade markets, means of processing the results of scientific and economic experiments, i.e. in automating regularly repeated calculations of large amounts of numerical and textual data representing tabular structures. The most popular spreadsheet editors are Lotus1-2-3 Quatto Pro, Microsoft Excel, Super Calc, etc.
Change
Sheet
Document No.
Signature
the date
Sheet
60 7
Database management systems(DBMS) allow you to work with large amounts of structured data - databases (as a rule, these are tabular structures). The functions of the DBMS include: description of data, access to data, search, selection of data according to certain criteria. Most modern DBMS allow you to create small programs data processing in built-in languages, have design capabilities that allow you to create a report based on the collected and processed data. Even low-skilled users can easily work with such DBMS, since all actions in them are carried out using menus and other interactive tools. However, it is often necessary to solve problems in which many various kinds objects and, accordingly, many information arrays connected with each other by various relationships. In such cases, it is necessary to create specialized Information Systems, in which the necessary data processing is performed in the most natural way for users with a convenient presentation of input data, output forms, graphs and charts, search queries, etc. To solve such problems, more complex DBMS are used, which allow using special tools (usually programming languages) to describe data and actions with them. An example program of this class is Microsoft Access.
Graphic editor allow you to create and edit pictures on your computer screen. These include raster and vector graphics editors, 3D graphics processing programs (Z D - editors). Bitmap editors use bitmaps to represent images, i.e. a collection of dots that have their own color and brightness. It is convenient to process photos and objects with soft color transitions in them. The basis of the vector representation is the line (its equation). Vector editors are convenient for working with drawings and hand-drawn pictures. Three-dimensional graphics editors are used to create spatial graphic compositions, allow you to trace the interaction of three-dimensional objects with each other and three-dimensional objects with a light source.As a rule, the user is given the opportunity to draw lines, curves, color areas of the screen, create inscriptions in various fonts, etc. Most editors allow you to process images obtained using scanners, as well as display the resulting pictures in such a way that they can be included in a document prepared using a text editor or publishing system. Some editors provide the ability to capture images of three-dimensional objects, convert raster images to vector format, professional color processing tools, etc.
Change
Sheet
Document No.
Signature
the date
Sheet
62 8
Solution softwareapplied mathematical(statistical) problems allow you to perform mathematical calculations: solving equations and systems of equations, etc., some packages allow you to perform analytical (symbolic) calculations: differentiation, integration, etc. Some of them allow you to display graphs of functions (given in tabular or analytical form), surface level lines, scatter diagrams, etc. This type of software includes programs such as matcad, matlab.
Separate programs, being a powerful tool for solving a range of applied problems, cannot fully satisfy the user. For example, it can be convenient to process a data sample provided by a DBMS using spreadsheets; the results, presented in the form of visual tables, can be placed in a report, which is a text document; which was compiled in a word processor. For the joint work of several programs, the unification of the formats of the processed files is also required. Such software packages are calledintegrated software. The most common product of this class is the package MS office. Integrated systems combine the capabilities of a database management system, a spreadsheet, a text editor, a business graphics system, and sometimes other capabilities.
translators usually work resident, i.e. in any text in a foreign language, you can highlight the fragment to be translated, and after pressing a certain key combination, a window with the translation or possible translation options for the word is presented.
Games very common, they are created great amount. Among them, the following typical scenarios can be distinguished: proactive games (for mastery), gambling, strategies, logic games, educational games.
Entertainment application programs that allow you to view slides, listen to sound files, video files.
Application software deals with the solution of narrower tasks, as well as tasks of a professional nature in various subject areas. special purpose, which includes: information systems, expert systems, computer-aided design systems, etc.
Change
Sheet
Document No.
Signature
the date
Sheet
63 9
Information Systems(IS), provide ample opportunities in:
Enterprise management is a warehouse, office workflow;
Accounting - these are systems that have the functions of text, spreadsheet editors and DBMS. Designed to automate the preparation of initial accounting documents, enterprises and their accounting, regular reports on the results of production, economic and financial activities in a form acceptable to tax authorities, extra-budgetary funds and statistical accounting authorities;
Analysis of economic and financial activities; they are used in banking and exchange structures. They allow you to control and predict the situation on the financial, trading markets and commodity markets, analyze current events, prepare reports.
Expert systemsrepresent further development systems, database management. They are designed to analyze data stored in knowledge bases. Unlike DBMS, which allow data manipulation operations, expert systems perform logical data analysis and have self-learning functions.
Computer-Aided Design Systemsallow drawing and designing various mechanisms using a computer, they are used in mechanical engineering, construction, architecture. They allow you to create drawing documentation adapted to a specific subject area, and also have reference books, calculation tools. Widespread programs such as AutoCAD, ArchCaAD, etc.
Change
Sheet
Document No.
Signature
the date
Sheet
5.2 maintenance and repair of computer systems
Unstable operation of the computer can happen due to malfunctioning coolers. The second reason for a malfunction of the computer is the breakdown of the power supply. A malfunction of the power supply can manifest itself as visible and hidden. With a visible malfunction of the unit, the computer does not show any signs of operability when turned on, the coolers do not work and the LEDs do not shine. With a hidden malfunction of the unit, unstable computer operation, sudden system freezes, spontaneous reboots, and errors during operation are observed. The power supply is the most loaded part of the computer and, in addition, is subjected to additional influences due to network instability in the form of natural voltage surges and natural ones during a thunderstorm. Therefore, it is recommended to turn off the computer and turn off the power during a thunderstorm. You can work on a laptop during a thunderstorm provided it is powered by a battery and connected to the Internet via Wi - Fi .
A malfunction of the RAM memory leads to unstable operation of the computer. Even positive results of testing by special programs cannot 100% guarantee that the memory is working, and the only way to verify the reliability is to replace the memory bar with a known good one. If there is more than one bar, then taking out one at a time, you can thus perform a check. If there are no failures, then the removed memory bar is to blame.
There are cases of unstable operation of the computer hard drive (hard drive). But, as a rule, if the hard drive malfunctions, even before the systems start loading, an error message is displayed about reading from the disk. Sometimes the hard drive starts making sounds. If the system boots and there is a suspicion of a hard drive malfunction, then you need to test it for bad sectors and set a ban on writing to these sectors. After a while, check again if new bad sectors appear, then the hard drive will have to be replaced.There are programs that allow you to physically make a copy of the hard drive installed in your computer to a new one, of any capacity. Then you do not have to spend time reinstalling programs and drivers.
Change
Sheet
Document No.
Signature
the date
Sheet
2 66
5.3 application of computer equipment repair skills
The most complex and responsible work of an employee of the maintenance department is the repair and maintenance of computers, so we will consider in detail the search and elimination of their malfunctions.
Computer breakdowns are usually divided into two groups: hardware-related and software-related. The first step is to determine which group of faults each specific case belongs to.
Hardware-related problems usually manifest themselves even before the operating system loads. Some of them can be detected using the so-called POST messages. The process of booting a computer begins with self-diagnosis, during which hardware failures are looked for. After that, special messages are sent to the user that indicate the health or malfunction of computer components. The decoding of these messages can be found in the motherboard manuals or on the manufacturer's website. BIOS . Table 1, are given for example POST popular BIOS AwardBIOS, which sends its messages as beeps.
Table 1 - AwardBIOS beeps
|
One short beep |
Successful POST testing |
|
Single signal with no picture |
Video card failure |
|
One long and one short beep |
RAM problems |
|
One long and two short |
Incorrect monitor connection or video card malfunction |
|
One long and three short beeps |
Keyboard testing error, controller malfunction |
|
One long and many short beeps |
Non-alternative BIOS corruption option |
|
Two short |
CMOS settings failure, or some non-critical error |
|
Three long |
Motherboard failure |
|
Permanent long |
Incorrect connection or memory failure, or mismatch with the motherboard |
|
Permanent short |
Power supply is defective |
|
The complete absence of any signals |
Power supply is defective |
Change
Sheet
Document No.
Signature
the date
Sheet
It should be noted that in modern motherboards it is possible to output POST messages to the LED indicators built into the board.
After receiving the corresponding signal, it is necessary to replace the defective part.
However, you should not rely entirely on the computer's self-diagnostic capabilities, as they only allow you to highlight critical errors in the equipment. It is impossible to isolate such malfunctions as, for example, a violation of the heat sink of the processor or video card.
After the computer passes self-diagnosis, the operating system starts loading. At this stage, most often, either a damaged hard drive or a damaged area of \u200b\u200bthe boot disk makes itself felt. The computer screen usually displays an inscription about the impossibility of booting from the hard disk. In this case, it is necessary to check the hard drive with the appropriate software. If the tests pass successfully, you must either reinstall or try to restore the computer's operating system.
After loading the operating system, software-related errors most often manifest themselves. Their range is so large that it requires consideration in each individual case.
Consider the symptoms of hardware problems that manifest themselves after the operating system has started.
If artifacts appear or the image disappears, then this indicates errors associated with the video subsystem. In some cases, reinstalling the video card drivers can help, in others it may indicate, for example, damage to the video memory or graphics processor.
If file reading errors are observed, then this undoubtedly indicates a malfunction of the data storage system.
Change
Sheet
Document No.
Signature
the date
Sheet
Errors that appear during the execution of the program sometimes indicate a malfunction of the RAM. It is recommended to check it with the appropriate software.
If the computer spontaneously restarts or freezes under the load of calculations, this may indicate a malfunction of either the central processor or its cooling. At the same time, one should not lose sight of the fact that errors of this kind may appear due to a malfunction, or insufficient power of the power supply.
An important part of the operation of the computer is its prevention in order to maintain health and speed.
Prevention is better to start with an external examination of the computer. Make sure that the computer case is not damaged or dented. Next, remove the housing cover and remove dust. This can be done either manually, for example, using a brush, or using a special installation. A similar installation is shown in Figure 3. It is successfully used in the maintenance department of the ITC.
Change
Sheet
Document No.
Signature
the date
Sheet
The installation consists of a hood, a semi-closed box and two vacuum cleaners. It is recommended to remove as many components as possible, in this case, the cleaning can go better. The first step is to suck up the dust, and blow out the rest. After this treatment, you can wipe the case with a dry cloth.
Change
Sheet
Document No.
Signature
the date
Sheet
CONCLUSION
She did an internship at an educational institution ZabGK them. M.I. Agoshkova
At the beginning of the industrial practice, she got acquainted with the activities of the college and its employees. Received a safety briefing. During the practice, she mainly worked with the replacement of parts and the installation of programs.
During my internship I gained experience in PC repair. I consolidated and improved my knowledge while working with programs. Performed tasks: reinstalling the OS, replacing the components of the system unit, as well as replacing and repairing external devices. Work at the enterprise gave practical skills of a programmer technician. I really enjoyed working in a close-knit team. This practice is very useful for further study and work, as a lot of skills, knowledge and skills have been obtained.
Thus, the work experience is a test of the knowledge gained during the training, and the opportunity to learn a lot about your profession.
Change
Sheet
Document No.
Signature
the date
Sheet
PP.03 Maintenance and repair of computer systems and complexes
BIBLIOGRAPHY
Braude, E. D. Software development technology / E. D. Braude. - St. Petersburg: Peter, 2010. - 260s.
Gagarina, L.G. Software development technology / L.G. Gagarina, E.V. Kokoreva, B.D. Visnadul; edited by Professor L. G. Gagarina. M.: - FORUM, 2011. - 315s.
Gagarina, L.G. Development and operation of automated information systems: textbook. allowance / L.G. Gagarina, D.V. Kiselev, E.L. Fedotova; ed. prof. L.G. Gagarina. - M.: ID Forum: Infra - M, 2013. - 384 p.
GOST 34.602-89 Technical task to create an automated system.
GOST 19.201-78 Terms of reference. Requirements for content and design.
Leonenkov, A. V. Self-tutor UML / A.V. Leonenkov. - St. Petersburg: BHV, 2010.-304p.
McConnell, S. Perfect Code / S. McConnell. - St. Petersburg: Peter, 2010.- 896s.
Olifer, V.G. Computer networks. Principles, technologies, protocols / V.G. Olifer, N.A. Olifer. - St. Petersburg: Peter, 2012. - 960s.
Popov, I.I. Computer networks: Textbook for students of institutions of secondary vocational education / I.I. Popov, N.V. Maksimov - M.: FORUM: INFRA-M, 2011. - 448s.
Homonenko, A.D. Databases: textbook for higher educational institutions/ ed. HELL. Homonenko. - St. Petersburg: Korona-Vek, 2010. - 416 p. Popov, I.I. Computer networks: a textbook for students of institutions of secondary vocational education / I.I. Popov, N.V. Maksimov - M.: FORUM: INFRA-M, 2013. - 516 p.
Olifer VG, Computer networks. Principles, technologies, protocols / V.G. Olifer, N.A. Olifer. - St. Petersburg: Peter, 2012. - 685s.
Gagarina, L.G., Development and operation of automated information systems: textbook. allowance / L.G. Gagarina, D.V. Kiselev, E.L. Fedotov: ed. prof. L.G. Gagarina. - M.: ID Forum: Infra - M, 2010. - 384 p.
Homonenko, A.D. Databases: a textbook for higher educational institutions / A.D. Homonenko, V.M. Tsygankov, M.G. Maltsev: ed. HELL. Homonenko. - St. Petersburg: Korona-Vek, 2010. - 416 p.
Additional sources:
Basakov, M.I. Certification of products and services with the basics of standardization and metrology / M.I. Basakov. - St. Petersburg: Peter, 2013. - 256s.
Blagodatskikh, V. A. Standardization of software development / V. A. Blagodatskikh, V. A. Volnin, K. F. Poskakalov. - M.: Finance and statistics, 2012. - 288s.
A practical guide for smart users and novice developers / A. Bondar. - St. Petersburg: BHV-Petersburg, 2011. - 592s
Change
Sheet
Document No.
Signature
the date
Sheet
PP.03 Maintenance and repair of computer systems and complexes
computer Borri, H. Firebird : database developer's guide / H. Borri. - St. Petersburg: BHV-Petersburg, 2013.- 1104 p.
Vendrov, A.M. Designing software for economic information systems / A.M. Vendrov. - M.: Finance and statistics, 2014. - 180s.
Grekul V.I. Design of information systems. http://www.intuit.ru
Hooke, M. Hardware local networks: Encyclopedia / M. Guk - St. Petersburg: Peter, 2011. - 576s.
Kovyazin, S. Mir InterBase / S. Kovyazin, S. Vostrikov. - M.: KUDITS - IMAGE, 2013. - 496 p.
Lavrovich, V., Kostyuchenko, A. Consumer Rights Protection Standards // Standardization. - 2011.- No. 5.- C.45-47
Lipaev, V. Selection and evaluation of software quality characteristics. Methods and standards / V. Lipaev. - M.: Sinteg, 2012. - 228s.
Olifer, V.G. Fundamentals of data transmission networks: a course of lectures / V.G. Olifer, N.A. Olifer. - Internet University of Information Technologies - INTUIT.RU, 2012.
Sorokin, A.V. Delphi . Database development / A.V. Sorokin. - St. Petersburg: Peter, 2010. - 2011. - 477p.
Bondar, A. InterBase and Firebird. A practical guide for smart users and novice developers / A. Bondar. - St. Petersburg: BHV-Petersburg, 2011. - 592 p.
Borri, H. Firebird : a database developer's guide / H. Bori. - St. Petersburg: BHV-Petersburg, 2012.- 1104p.
Vendrov, A.M. Design of software for economic information systems / A.M. Vendrov. - M.: Finance and statistics, 2012. - 180s.
Kovyazin, S. Mir InterBase . Architecture, administration and development of database applications in InterBase/Firebird/Yaffil / S. Kovyazin, S. Vostrikov. - M.: KUDITS - IMAGE, 2013. - 496 p.
Informational resources:
|
Magazine websites |
Programmer Access mode: http://jurnal-programmist.at.tut.by/ open systems Access mode: http://www.osp.ru |
|
educational sites |
1. Internet University of Information Technology Access mode: http://www.intuit.ru |
|
Portals |
1. Information and communication technologies in education Access mode: http://www.ict.edu.ru |
Change
Sheet
Document No.
Signature
the date
Sheet
PP.03 Maintenance and repair of computer systems and complexes
ATTACHMENT 1
Structure of ZabGK

Change
Sheet
Document No.
Signature
the date
Sheet
PP.03 Maintenance and repair of computer systems and complexes
Other related works that may interest you.vshm> |
|||
| 11736. | Maintenance and repair of vehicles at service stations | 410.93KB | |
| Road transport, unlike other types Vehicle is the most massive and convenient for the transportation of goods and passengers over relatively short distances. It has greater maneuverability, good adaptability and cross-country ability in various climatic and biographical conditions. Road transport plays an important role in the country's transport system. The work of road transport is provided normal functioning enterprises. | |||
| 18032. | Maintenance and current repair of motor vehicles with the development of a site for the maintenance and repair of the chassis and brake system of the vehicle | 763.12KB | |
| Determination of the share of labor intensity of guard work. Calculation of the labor intensity of maintenance work and TR. The choice and justification of the forms and methods of work of the post. Instructions for use of the developed device... | |||
| 5380. | Development of a training stand The device and principle of operation of the printer as a means of improving the quality of training students in the specialty Maintenance of computer equipment and computer networks | 243.46KB | |
| Printers are classified according to five main positions: the principle of operation of the printing mechanism, the maximum size of a sheet of paper, the use of color printing, the presence or absence of hardware support for the PostScript language, as well as the recommended monthly load. | |||
| 15285. | Design and maintenance of the AI-24 engine | 166.53KB | |
| The TG-16M turbine generator set is an autonomous unit and consists of a GTD-16M gas turbine engine, a gearbox, a GS-24A-ZS DC generator and systems that ensure the start-up and operation of the unit. The GTD-16M gas turbine engine consists of a centrifugal compressor with a one-way air inlet, an annular combustion chamber, a single-stage gas turbine and an exhaust pipe. | |||
| 12601. | Maintenance and repair of equipment of compressor station No. 14 "Privodino" | 442.83KB | |
| Based on the special climatic conditions of the area where the compressor station is located and technical studies, methods for maintaining and repairing this technological enterprise were proposed. The paper considers measures aimed at protecting environment, labor protection, requirements for compliance with industrial safety for the working personnel of the enterprise. An assessment of potential sources of technogenic impacts on the environment has been carried out. | |||
| 10039. | Development of software modules for computer systems | 475.4KB | |
| The Actions on Matrices software tool was designed and implemented, a graphical interface was developed for it in the Microsoft Visual Studio Ultimate 2013 С# environment. The software product allows you to study the structure and syntax of new programming languages. | |||
| 8356. | Types of software architecture of network information systems. Open systems architecture. Fundamentals of the Internet. Internet Services. Internet connection | 25.51KB | |
| This is networking with so-called thick clients m. In this case, all calculations take place on servers and client computers only display information received from the network and it becomes possible to work on a network with ultra-thin clients, for example, with small mobile devices. Packet is a unit of information transmitted between network devices as a whole. This level defines the range of applied tasks implemented in a given computer network, providing access for applied processes to network services. | |||
| 6909. | Means of combating computer viruses | 7.6KB | |
| The presence of anti-virus programs and hardware protection provides the following options. Virus detection and protection programs Antivirus are types of special programs that are used to detect removal and protect against computer. Types of anti-virus programs: Programs detectors search for a signature characteristic of a particular virus in RAM and in files, and upon detection they issue a corresponding message. | |||
| 1653. | Development of an online store of computer components | 521.4KB | |
| From the point of view of a system administrator, whose functions include maintaining and operability Internet shop daily updating, etc. Requires a minimum of operating and administration costs and, therefore, the need for significant time and financial resources during administration, does not occur. | |||
| 9694. | Organization and maintenance of information networks at the enterprise | 242.6KB | |
| There is a rather extensive class of information processing systems in the development of which the security factor plays a primary role, for example, banking information systems. IS security is understood as the security of the system from accidental or deliberate interference in the normal process of its functioning from attempts to steal unauthorized information, modification or physical destruction of its components. An information security threat is understood to mean events or actions that can lead to a distortion ... | |||
Send your good work in the knowledge base is simple. Use the form below
Students, graduate students, young scientists who use the knowledge base in their studies and work will be very grateful to you.
Posted on http://www.allbest.ru/
Ministry of Informatization and Communications of the Republic of Tatarstan
State budgetary educational institution of secondary vocational education "Kazan Electrotechnical School of Communications"
about the internship
Maintenance and repair of computer systems and complexes
Completed by: Davletshin E. A., student of group 405 KSK
Kazan, 2014
|
Workplace |
Mark of the head of practice from the enterprise |
|||
|
Workplace coaching |
||||
|
Safety engineering. Rules of behavior. |
||||
|
Introductory tour of the enterprise. |
||||
|
Introduction to equipment. |
||||
|
Consultation |
||||
|
Installing the printer. |
||||
|
Cleaning the printer. |
||||
|
Setting up the printer's network. |
||||
|
Installing printer software. |
||||
|
Configuring the printer software. |
||||
|
Consultation |
||||
|
Refill printer cartridges. |
||||
|
Printer Diagnostics. |
||||
|
PC Diagnostics. |
||||
|
Setting the print media. |
||||
|
Test print on the printer. |
||||
|
Consultation |
||||
|
Installing the plotter. |
||||
|
Cleaning the plotter. |
||||
|
Setting up the plotter's network. |
||||
|
Configuring the software for the plotter. |
||||
|
PC Diagnostics. |
||||
|
Consultation |
||||
|
Printer Diagnostics |
||||
|
Printer Diagnostics |
||||
|
PC Diagnostics. |
||||
|
Consultation |
||||
|
Consultation |
||||
|
Consultation |
Head of Practice ______________________
Introduction
2.1 Maintenance and repair of computer systems and complexes
Conclusion
Introduction
Field trip goals
The objectives of the production practice in the direction of 230000 Informatics and Computer Engineering in the specialty 230113 Computer Systems and Complexes are:
§ formation and development of general and professional competencies in the field of the chosen specialty,
§ acquisition and development of the necessary skills, abilities and experience practical work to solve professional problems in the conditions of a particular enterprise (organization) of the city and district
§ organization of independent professional activity, socialization in concrete form activities.
Work practice tasks
The objectives of the internship in the direction 230000 Informatics and Computer Engineering in the specialty 230113 Computer Systems and Complexes are:
§ consolidation, deepening and expansion of the acquired theoretical knowledge, skills and abilities;
§ mastery professional competencies, production skills and new methods of work;
§ mastering the norms of the profession in the motivational sphere: awareness of motives and spiritual values in the chosen profession;
§ mastering the basics of the profession in the operational sphere: familiarization and assimilation of the methodology for solving professional tasks (problems);
§ study of different aspects of professional activity: social, legal, psychological, hygienic, technical, technological, economic.
Place and time of internship
Location - KNPO VTI
Practice leader from the organization - Gimadiev Rustem Ferlisovich
Structure and content of work practice
Industrial practice is an obligatory type production work, is included in the section "Educational and industrial practice" of the Federal State Educational Standard of secondary vocational education in the direction of preparation 230000 Informatics and computer technology, specialty 230113 Computer systems and complexes.
The total labor intensity of the production practice is 5 weeks, which is 180 hours.
This practice includes the following modules:
PM.03 Maintenance and repair of computer systems and complexes
MDK.03.01 Maintenance and repair of computer systems and complexes
flash drive software
Chapter I a brief description of enterprises
1.1 Brief description of the enterprise
Acquainted with production activities enterprise / organization and briefly describe it.
1.2 Scheme of organization of the enterprise structure
Describe the structure and infrastructure of the organization. The system of relationships between its individual divisions, the main areas of activity, relations with partners.
Draw the structure of the enterprise and the scheme of interaction between structural divisions and partners using graphic editors.
1.3 Computer base and enterprise software
Familiarize yourself with the office equipment and software used in the enterprise. Analyze the feasibility of their choice. Compile a joint register computer technology and software. Describe the computer (processor, memory, video, etc.) and software (OS name, names and versions of application, service and other programs).
1.4 Information technologies and systems used at the enterprise
Familiarize yourself with the specialized programs used in this enterprise / organization and describe them. Run short description software, do a search and comparative analysis with analogues (highlighting the advantages and disadvantages of the software used).
1.1 1.5 Occupational health and safety
Structure of GBOU SPO "Kazan Electrotechnical College of Communications"
Register of computer hardware and software
|
Name |
Location |
Software license, validity period |
||||
|
Secretary's computer |
Celeron 336 processor |
Room 206, building A |
MSDN until 10/17/2013 |
|||
|
ASUS motherboard integrated with video and network 100 Mb |
OpenOffice.org 3.2 |
LGPL perpetual |
||||
|
RAM 2048Mb |
CorelDRAW Graphics Suite X4 |
|||||
|
Hard disk 160.0 Gb |
Adobe Creative Suite 4 |
perpetual, educational |
||||
|
Power supply 350W |
Autodesk® 3ds Max® Design 2010 |
perpetual, educational |
||||
|
Mouse PS/2, Genius NetScroll Eye, (optical, 2 buttons + 1 scroll, PS/2) |
LGPL perpetual |
|||||
|
PS/2 keyboard |
||||||
|
NERO 6 Enterprise Edition |
volume licenses, perpetual |
|||||
|
Monitor 19" Xerox XM7-19W TFT |
||||||
|
ESET NOD32 Antivirus |
||||||
|
Mozilla Thunderbird 3.0.4 |
LGPL perpetual |
|||||
|
ABBYY PDF Transformer 2.3 |
||||||
|
Double GIS 3.0 |
||||||
|
Chief Engineer's Computer |
Processor Pentium Dual Core E5400 OEM (2.70GHz, 800FSB,2Mb, EM64T, LGA775) |
Room 208, building A |
MS Windows XP Professional sp3 |
|||
|
Motherboard MSI G41M4-F (S775, iG41, DDR2, PCI-E16x, SVGA, SATA, GBLan, mATX, Retail) |
OpenOffice.org 3.2 |
|||||
|
RAM DDRII 2048Mb (pc-6400) 800MHz Kingston |
List of installed software
install.txt (CCleaner)
"1C: Enterprise. Accounting" 7.7 (network version) 02/02/2012
"1C: Enterprise. Calculation" 7.7 (network version) 02/02/2012
1C:Enterprise 8.2 (8.2.11.232) 1C 09/28/2010 249.00 MB 8.2.11.232
1C:Databases 09/09/2012
7-Zip 4.42 11/22/2007
ABBYY FineReader 9.0 Corporate Edition ABBYY 02/15/2008 288.00 MB 9.00.710.5522
ACDSee Pro 2.5 ACD Systems International 01/12/2010 91.37 MB 2.5.358
Adobe Audition 3.0 Adobe Systems Incorporated10/12/2009 3.0
Adobe Flash Player 11 ActiveX Adobe Systems Incorporated 09/08/2012 11.3.300.271
Adobe Flash Player 11 Plugin Adobe Systems Incorporated 09/08/2012 11.3.300.271
Adobe Photoshop 7.0 Adobe Systems, Inc. 08/25/2010 7.0
Adobe Reader 8.1.1 Adobe Systems Incorporated 01/14/2008 86.41 MB 8.1.1
Advanced Archive Password Recovery Elcomsoft LLC 09/09/2012 4.0
Advanced IM Password Recovery (remove only) 09/09/2012
Ashampoo HDD Control 2 v.2.1.0 Ashampoo GmbH & Co. KG 09/08/2012 2.1.0
Ashampoo WinOptimizer 9 v.9.04.31 Ashampoo GmbH & Co. KG 09.09.2012 09.04.31
AST-Test_Player 3.0.4001 AST-Centre 11/20/2007
ATI - Uninstall Utility 11/20/2007 6.14.10.1017
ATI Catalyst Control Center 2.007.0815.2325
ATI Display Driver 06/11/2008 8.401-070815m-052022C-ATI
AVS DVD Player version 2.2 Online Media Technologies Ltd. 04/09/2008
AVS DVDMenu Editor 1.2.1.20 Online Media Technologies Ltd. 05/13/2008
AVS DVDtoGO 1.4.2 Online Media Technologies Ltd. 04/09/2008
AVS Video ReMaker 2.4 Online Media Technologies Ltd. 05/13/2008
AVS4YOU Software Navigator 1.2 Online Media Technologies Ltd. 05/13/2008
Canon LASERSHOT LBP-1120 09/09/2012
CCleaner Piriform 08/22/2012 3.22
CheckXML 07/26/2010
Corel VideoStudio 12 Corel Corporation 11/10/2010 12.0.0.0000
CrazyTalk Avatar Creator Reallusion 09/25/2009 4.5.3214.3
CrazyTalk Cam Suite Reallusion 09/25/2009 1.0
Facemoods Toolbar 04/11/2011
FileZilla Client 3.2.1 02/13/2009 3.2.1
Firebird 1.5.3.4870 Firebird Project 06/02/2008
FoxTab PDF Converter FoxTab 04/11/2011
Google Google Chrome Inc. 29.10.2009 21.0.1180.89
Guard.Mail.ru Mail.ru 14.06.2011
Guardant driver 08.09.2012
HPSSupply Organization name 01/29/2010 0.96 MB 2.2.0.0000
Startup Registry
startup.txt (CCleaner)
Yes HKCU:Run AlterGeoUpdater AlterGeo C:\Documents and Settings\All Users\Application Data\AlterGeo\Update for Html5 geolocation provider\html5locsvc.exe
Yes HKCU:Run ctfmon.exe Microsoft Corporation C:\WINDOWS\system32\ctfmon.exe
Yes HKCU:Run ICQ ICQ, LLC. "C:\Program Files\ICQ7.2\ICQ.exe" silent loginmode=4
Yes HKCU:Run IncrediMail IncrediMail, Ltd. C:\Program Files\IncrediMail\bin\IncMail.exe /c
Yes HKCU:Run MSMSGS Microsoft Corporation "C:\Program Files\Messenger\msmsgs.exe" /background
No HKCU:Run ooVoo.exe ooVoo LLC C:\Program Files\ooVoo\oovoo.exe /minimized
HKCU:Run swg "C:\Program Files\Google\GoogleToolbarNotifier\GoogleToolbarNotifier.exe"
Yes HKLM:Run AlterGeoUpdater AlterGeo C:\Program Files\AlterGeo\Html5 geolocation provider\html5locsvc.exe
Yes HKLM:Run Ashampoo HDD-Control 2 Guard Ashampoo Development GmbH & Co. KG "C:\Program Files\Ashampoo\Ashampoo HDD Control 2\AHDDC2_Guard.exe"
No HKLM:Run autodetect C:\WINDOWS\system32\SupportAppXL\AutoDect.exe
Yes HKLM:Run AVP Kaspersky Lab ZAO "C:\Program Files\Kaspersky Lab\Kaspersky Internet Security 2012\avp.exe"
No HKLM:Run BluetoothAuthenticationAgent Microsoft rundll32.exe bthprops.cpl,BluetoothAuthenticationAgent
Yes HKLM:Run CAP3ON CANON INC. C:\WINDOWS\system32\spool\drivers\w32x86\3\CAP3ONN.EXE
Yes HKLM:Run CAPON CANON INC. C:\WINDOWS\system32\Spool\Drivers\w32x86\3\CAPONN.EXE
No HKLM:Run facemoods facemoods.com "C:\Program Files\facemoods.com\facemoods\1.4.17.6\facemoodssrv.exe" /md I
Yes HKLM:Run Guard.Mail.ru.gui "C:\Program Files\Mail.Ru\Guard\GuardMailRu.exe" /gui
Yes HKLM:Run MAgent Mail.Ru C:\Program Files\Mail.Ru\Agent\magent.exe -LM
Yes HKLM:Run snp2std Sonix C:\WINDOWS\vsnp2std.exe
No HKLM:Run UVS12 Preload Ulead Systems, Inc. C:\Program Files\Corel\Corel VideoStudio 12\uvPL.exe
No HKLM:Run vmware-tray VMware, Inc. C:\Program Files\VMware\VMware Workstation\vmware-tray.exe
No Startup Common Beeline USB Modem.lnk C:\PROGRA~1\ZTEMF1~1\USB-~1\UIMain.exe
Yes Startup Common Status Window Canon LASER SHOT LBP-1120.LNK CANON INC. C:\WINDOWS\system32\spool\drivers\w32x86\3\CAP3LAK.EXE
No Startup Common Status Window Canon LBP-810.LNK CANON INC. C:\WINDOWS\system32\spool\drivers\w32x8
Chapter II. Description of the technology for performing a practical task
2.1 PM. 03 Maintenance and repair of computer systems and complexes
Theoretical material is selected according to an individual practical task
Practical material
An individual practical task is selected according to the completed module: MDK.03.01 Maintenance and repair of computer systems and complexes.
2.2 Individual practical task
Repair of USB drives. The main types of faults.
Modern USB drives and memory cards are not very reliable. Cases break in them, connectors and power circuits fail, microcircuits fail, and finally, the firmware flies and defects multiply. Many users have already experienced at least one flash drive failure, after which they thought: is it possible to fix it yourself?
Practice shows that 50-60% of malfunctions are treated simple methods that do not require special training and equipment.
Consider the main types of USB drive failures, their causes and the possibility of self-repair.
1. Mechanical failures
For flash drives, these are case defects, breakage of the cap and other moving parts, damage to the USB connector and the printed circuit board. SD cards have a layering of the case and the loss of a slider that blocks the entry in the reader. Both drives do not like moisture and do not work when flooded.
With a bent or broken USB connector, the flash drive is inoperable, at best it is recognized once and will not live long. A cracked board requires repair, not always successful. An SD card with a slider that has flown out becomes read-only, nothing can be written to it. SD with a delaminated case can be difficult to insert into and remove from the slot, the use of force only worsens the situation.
The cause of mechanical damage is mostly user negligence. Flash drives are inserted crookedly into the USB port of a computer or laptop, they are touched by a hand or foot. Outside the computer, flash drives are dropped on the floor, stepped on, etc. Drives get into the washing machine, under spilled coffee and just in the dirt. Folding and retractable structures suffer from excessive effort - their parts are worn out. Wear is accelerated in aggressive environments (e.g. in keychains). If the cap is lost, dust and moisture enter the USB connector, damaging the contacts.
Mechanical repair aims to restore the functioning and reliability of the flash drive. This is gluing or replacing the case, selecting a cap to replace the lost one, etc. At a loose USB connector, the mounting ears and the contacts themselves are soldered. A bent connector is straightened very carefully: adjacent tracks on the board may break, and the repair is complicated. On SD cards, instead of a lost slider, you can paste a piece of a match. Contacts are cleaned with a cotton swab with an alcohol-gasoline mixture. When working, you should avoid static - the cards are sensitive to it.
2. Electrical faults
This is primarily a failure of the controller, as well as defects in the piping elements - filters, resistors, capacitors, stabilizer, quartz. These parts have a break, short circuit, deterioration of parameters. Electrical faults include violations of current-carrying tracks and contacts with parts. Assembly defects often appear (cold soldering, etc.).
In such cases, the flash drive does not show signs of life, or it is defined in the OS as an “unknown USB device”. In particular, this happens with unreliable contact between flash memory chips and the board. With poor soldering, the device can only work in a certain position. It happens that defects appear only with heating, and a cold flash drive works fine. Gradually, the periods of working capacity are narrowed, reaching a complete failure.
Electrical damage to flash drives and memory cards can also include ingress of water and other liquids. The causes of electrical damage are power surges, static discharges, as well as overheating of drive parts, primarily the controller. So, with an increased voltage of 5 V, the flash drive heats up much more, and an intense data stream can finish it off. The manifestation of soldering defects is facilitated by mechanical loads, as well as drops and bumps. If the quartz cracked or moved away from the board, the flash drive is recognized as an “unknown device” and, of course, does not work. The same effect is given by the non-contact of the controller with the board.
This is in need of a hardware overhaul. With the help of a thin soldering iron and a technical hair dryer, soldering is strengthened, damaged contacts and tracks are restored. Defective parts are replaced. As for the “drowned” flash drives, they are treated similarly to other gadgets. The board is washed from salts and dirt, then immersed in isopropyl alcohol(it displaces water from the cracks) and finally dried with warm air.
3. Software malfunctions
This includes many cases when the flash drive has no visible damage, when connected to the USB port, it shows signs of life - it blinks with an indicator and is even recognized in the OS, but does not give access to data. The drive has the wrong capacity (zero, 1 MB, or a couple of terabytes), and any time it is accessed, the messages “Insert disk”, “No access to disk”, etc. are displayed.
The main reason is damage to the firmware, or firmware. The firmware includes an unchangeable controller microcode and service data in flash memory, which are updated quite often. Another cause of failures is failures of the flash memory itself. Each chip has a capacity reserve to replace faulty pages. Defect management is one of the main functions of the firmware, and if the intensity of reassignments exceeds the threshold, then a block is set. Sometimes a flash drive is blocked only for writing: the data is visible and readable, but when you try to delete a file or format it, the message "The disk is write-protected" is displayed. NAND memory is damaged when written, and reading in mild cases can be left.
5. Dispensary
Preventing damage is easier than fixing it. Proper use of flash drives and memory cards eliminates many problems. Here are some simple guidelines.
· The life of USB-drives is reduced by mechanical impacts, temperature changes, dampness and aggressive environments. Also among the threats are static discharges, strong electromagnetic fields and radiation. Protect flash drives from all this.
· Regularly check the file system of USB drives using the built-in OS tools - this eliminates most logical errors.
· It is undesirable to use it in intensive recording mode (working accounting bases) - its resource and reliability are falling.
・Memory cards in mobile devices remove them from the slot less often and do not work with them with a dead battery. Wait until operations are completed and turn off the power before removing.
· Remove USB sticks from the port only in a safe manner. The drive often fails when it is pulled out at the time of recording.
· If the flash drive becomes buggy (falls off, freezes, etc.) - do not rush to treat it with service utilities, they lead to data loss. First, copy important files to another medium, and only then proceed with the repair.
Conclusion
During the internship, practical skills were obtained in the installation of fire protection systems.
Hosted on Allbest.ru
Similar Documents
Computer base and enterprise software. Information technologies applied at the enterprise. Maintenance and repair of computer systems and complexes. Repair of the print head on the EPSON MFP. Register of computer technology.
practice report, added 04/26/2014
Diagnostics of hardware and network adapters of a personal computer. The main directions of troubleshooting. Diagnostic, preventive and anti-virus programs. Repair of peripheral devices, measuring devices.
abstract, added 01/28/2016
Creation of a system utility that works with the Windows registry; structure, functions and role of the registry. Software development: interface, structural scheme application window calls; implementation and testing of the program, procedure; module listing.
term paper, added 06/01/2013
Analysis of the processing of information entered into the FSIS "FBDA. List of subsystems of the FSIS "FBDA" to be modernized. Description of automated functions. Software development. Design of the user interface of this system.
thesis, added 11/18/2017
Repair and cleaning of a computer mouse and keyboard; diagnostics of the LCD monitor. Programs and utilities for testing CD/DVD drives. Maintenance of laser and inkjet printers. Recovery of the operating system, hard drive, motherboard.
practical work, added 07/20/2012
The concept and purpose of computer peripherals, their maintenance and repair. Features of image formation by matrix and inkjet printers. Structure and principle of operation laser printer, ways to check the quality of its printing.
thesis, added 11/26/2010
Technical and economic characteristics and organizational structure enterprises. Characteristics of the existing equipment accounting system for the company's customers. Implementation of the system "Accounting and analysis of maintenance of computer hardware and software".
thesis, added 04/08/2014
Repair and maintenance of printers, monitors, uninterruptible power supplies, computer mice. Installation and maintenance of the operating system. Assembling a computer from components. Software required by the technical department worker.
practice report, added 08/07/2013
Features of the design of modern hard drives, a system of operational monitoring of their condition. Types of magnetic disk defects. Malfunctions of the hardware part of the disk, the nature of their manifestation and the method of elimination. Symptoms of equipment failure.
term paper, added 10/10/2014
Characteristics of the enterprise for the maintenance of computer equipment and computer networks. Consideration of the structure, goals and objectives of the service department, organization of the workplace, forms of remuneration. Learning the rules of working with e-mail.
Complex or network) consists of technical and system maintenance of the system and its use for its intended purpose - for data processing. Maintenance ( technical operation) - ensuring the operability of the system by creating the required operating conditions (power supply, temperature, etc.) and carrying out preventive and repair work. The main indicator of the quality of maintenance is the availability of the system (components), which characterizes the proportion of "time during which the system (components) is operational. The increase in the availability of the system is achieved by reducing equipment downtime due to preventive and repair work. On the effectiveness of maintenance most significantly affect the following factors: 1) operating conditions of the system (power supply stability, temperature, cleanliness of the environment, etc.): 2) reliability and maintainability of the system, the degree of perfection of monitoring and diagnostic tools; 3) mode of service and qualification of service personnel; 4) completeness of data on failures and failures technical means. To improve the efficiency of maintenance, the systems provide for the accumulation of data on errors, failures and failures. Data is collected by recording the state of the system at the time of the error detected by built-in controls or programs. Data registration is performed by the operating system in a special system log - an area of a magnetic disk drive. Data from the system log is periodically or if necessary printed out and used by maintenance personnel to identify sources of errors, failures and failures in order to carry out preventive and repair work.
System maintenance
System maintenance (system maintenance) - ensuring the efficiency of using the system, aimed at reducing the cost of data processing, improving system performance, the quality of user service, etc. The main tasks of system maintenance: 1) selection and adaptation of operating systems, including system-wide software; 2) setting the operating system for the workload - the organization and selection of system operation parameters that provide the required quality of user service and maximum performance; 3) improving the configuration of the system - the composition of the device and the connections between them. All tasks of system maintenance are reduced to mutual coordination of the configuration, system operation mode and workload to ensure the required quality of user service - organizing the necessary data processing modes, increasing productivity, reducing response time and data processing cost. The choice of the operating system is made based on the configuration of the computing system (processor performance, RAM capacity, composition of external memory and input-output means), the need for data processing modes (concentrated, telecommunications, network, batch, interactive, etc.) and the main properties of the workload (composition and characteristics of tasks solved by the system). The operating system adapts to the configuration of the computing system and the needs of users by generating a variant that must contain the necessary device and memory management tools, data access methods, and provide the required data processing modes. In this case, the RAM and external memory are divided into areas provided to the system and application software. The system-wide software includes the necessary tools for automating programming, working out symbolic and graphic information, database management, teleprocessing, etc. The resulting version of the operating system determines the possible modes of functioning of the computer system and data processing with an accuracy of parameter values that set the level of multiprogramming, the value of the quantum of processor time, the number of system I / O processes and other indicators that are set and changed during the operation of the computing system by adjusting the operating system to the current workload.
Operating system setup
When generating an operating system, the workload can only be roughly predicted. Moreover, it changes over time. Therefore, the adjustment of the operating system to a real workload is carried out on a working computer system and is repeated many times. The purpose of tuning is to improve system performance and provide the required processing speed - the required response time. Tuning comes down to assigning operating system parameters: multiprogramming level, processor time quantum, buffer sizes, job and task scheduling algorithms, memory and device management algorithms, etc. containing monitors and means of processing measurement data. The functioning of the computing system is evaluated by the combination of the following characteristics: 1) resource intensity of the work performed, workload and system load; 2) loading of system resources and structural loading; 3) system-wide - performance, response time and process profiles. By analyzing the registered Characteristics, overloaded and underused system resources are identified and narrow places, negatively affecting performance and response time. Using the operating system settings, you can change the level and structure of resource loading, process profiles and, consequently, performance and response time. The effect achieved by changing the tuning parameters is predicted either heuristically, based on a priori ideas about the degree of influence of the parameters on the system characteristics, or using performance models. The way information is placed in system memory has a significant impact on performance and response time. Thus, the intensity of external memory access strongly depends on which operating system modules are declared resident and placed in RAM. The access time to magnetic disk drives significantly depends on the order in which data sets are placed on the drives and within each drive. With the help of monitors, the intensity of calls to each of the drives (data volume) and data set is determined, as well as the distribution of the intensity of calls by the cylinders of the drives. Due to the redistribution of data across volumes, uniform loading of external storage devices is ensured, and, consequently, the access time to external memory is reduced. 3a, by moving data sets within each volume, the access time to the drives is reduced. Systematic work on measuring and analyzing the functioning of the computer system and setting the operating system allows you to optimize the values of the tuning parameters. In this case, further tuning cannot provide significant improvements, and in order to improve performance, it is necessary to improve the system configuration: increase the number of devices or use devices with higher characteristics.
Computer system configuration
Improving the configuration of a computer system is carried out similarly to setting up an operating system. With the help of measurements, the necessary data on the functioning of the computing system are obtained, in particular, data on the loading of devices. If the load of individual devices or groups of relative devices is close to the limit and the operating system setting is not able to change the load, you need to increase the number of appropriate devices, for example, magnetic disk drives, communication channels, or use devices with the best performance. In order to evaluate the effect obtained by improving the configuration of the system, performance models are used, with the help of which the characteristics of the system are predicted and the optimal variant of the configuration development is revealed. Changing the configuration entails the need to work on adjusting the operating system to the new configuration and workload. The possibilities of evolutionary development of the configuration and improvement of the processing mode to meet changing requirements may be exhausted. Then there is a need for qualitative changes - a complete replacement of computers with a more productive or preferable one in terms of other characteristics. This task in the practice of systematic exploitation is called the problem of choice. In a rigorous formulation, the choice problem is a complex multi-parameter and multi-criteria optimization problem, the methods for solving which are far from complete. In practice, the problem is solved in terms of choosing from a certain number of industrially mastered or planned for release systems. The choice is based on resource estimates and experience in using available funds. For selection, the following data should be obtained: 1) on the use of available resources by tasks of various classes; 2) on the use of resources to provide various processing modes (batch, online).
Forecasting
The forecast of changes in the volume and composition of the load, processing modes and maintenance requirements should be based on the relevant organizational and technical and economic prerequisites. The complexity of forecasting lies in the fact that in order to obtain a reliable forecast, it is necessary to have data on the resource intensity of various classes of tasks and their impact on computer utilization indicators. To obtain such data, it is necessary to analyze the entire process of using computers in a particular field of application. The forecast of needs for computing resources is associated with planning and economic data, for example, with a planned change in the volume of output or the volume of design and other work. The prediction results should determine the required service rate for the main types of resources (processor and I/O device) for each task class and processing mode. The second step in the selection is to compare the predicted resource requirements with the characteristics of potential configurations. Initially, the processor performance is selected, which should be sufficient to process the task flow. The performance score is obtained by summing the service rate across different task classes for batch and online mode and operating system. Based on the score obtained, the nominal performance of the processor is selected. The choice of the input-output system configuration consists in determining the composition of peripheral devices, including channel equipment, sufficient for the predicted load. It is necessary that throughput I/O, primarily disk storage, was in line with the predicted I/O rate, given online response time limits.
Links
- Aven OI, Gurin NN, Kogan Ya. A. Quality assessment and optimization of computing systems. Moscow: Nauka, 1982.
- Larionov AM Computer systems, systems and networks. Leningrad: Energoatomizdat. Leningrad branch. 1987.
- Ferrari D. Performance evaluation of computing systems: Per. from English. M.: Mir, 1981.
Wikimedia Foundation. 2010 .
Everything man-made that is of value to man must be maintained in order to fulfill its functions. This is especially true for computer technology. So, it is necessary to ensure that all components work, that a lot of dust does not settle inside closed boxes, and much more. You have to watch so that even the wires and connectors do not move away from their places. In order to avoid problems, it is initially necessary to design and install everything necessary. Manufacturers do a good job with these tasks (if we talk about computers and smartphones). But what can be said about why additional intervention is needed? Here, for example, maintenance of computer networks and systems. After all, this is not an easy task! By the way, depending on the complexity, sometimes they say "maintenance of computer and intelligent systems and networks." What is it, how does it happen, what skills are needed? Let's talk about this.
What is meant by service and systems?
This is a necessary, though not feasible task for everyone, which consists in designing, installing and laying cables, as well as setting up the operation of equipment. If you have experience, maintaining computer systems and networks is not difficult. When deciding to do everything with your own hands, you need to decide on the point from which the connection will go, along which route, how it will all be attached, and much more. When setting up computer systems, it is also necessary to solve a whole range of issues: what software to use, how to optimize the operation of equipment, what restrictions to set, how to connect to a local / global network. See? There is a lot to work on. And it's not as easy as it might seem at first glance. Therefore, in order to avoid problems with sagging and interfering wires, you have to decide how everything will be done, fixed, so as not to affect the aesthetic appearance of the room. It should be noted that it makes sense to lay a computer network if more than 3 are used. The fact is that if there are two of them, then the most rational solution is to connect directly. When there is only one computer at all, then there is no need to talk about anything.
Maintenance of computer systems and networks - what is it and how is it implemented?

Let's focus more on the technical part. Three main components of computer network maintenance:
- Complex design.
- Installation of cable routes.
- Wiring.
Speaking about the maintenance of computer networks, it is impossible to make such exact list because it is potentially huge. Let's focus on the most important elements:
- Setting up the necessary software.
- Optimization of the operating system, RAM, registers.
- Checking the functioning of the hardware using the BIOS and troubleshooting possible problems.
- Cleaning disks from trash that has not been used for a long time.
- Carrying out diagnostic and restoration work.
Integrated design

What is meant by this? This includes building a plan for what will be done and how. The following technologies can be used:
- Using
- Using wireless technology.
- The use of optical developments.
It is necessary to consider what and how should be laid, what will be used for fasteners and what are the best ways. It also provides for the presence of routers, routers, servers and many other pieces of computer equipment, which is necessary for the full operation of large networks.
Installation of cable routes and laying of wires
This is necessary for a more detailed implementation decision:
- Use of trays or cable racks.
- The use of plastic boxes.
- The use of corrugated pipes.
- Application of sewer technology.
Diagnostics, cleaning and recovery of computer systems

First, about diagnostics. It is necessary to check all disks for errors, the same action applies to RAM. Then, with the help of special software, registers are cleaned and applications that are not used for long periods of time are removed. Also, defragmentation of information that is in the physical ones is carried out. And at the very end, they check and restore the health of damaged disk sectors (if these problems exist).
Work optimization
An important component when talking about the maintenance of computer networks and systems. The fact is that for this it is necessary to revise the work of the register and clean it of garbage, check the applications that run with the operating system and negatively affect the download speed. At the same time, you can configure the processor to show its maximum (but the negative side of this approach is increased energy consumption and a 10-20% reduced service life).
Also, to get more speed, it will be useful to turn off visual effects and, accordingly, speed up the execution of your own. This procedure will be especially useful for office computers, which usually cannot boast of significant speed. There are still optimization possibilities, but they are more related to individual programs, such as developing special settings or working with system files in order to ensure the future execution of the application at the hardware level.
Choice between self-employment and hired company
This kind of work is still desirable to be done by professionals. When creating everything with your own hands, you need to take into account that you may have to drill the walls (which implies the presence of the appropriate tool) and you need a supply of wires and connecting parts. Maintenance of computer systems and networks at home is much easier than at work. You can forget about all this if the work is done by professionals, but there is the problem that they need to pay an amount that is approximately 1000-2000 rubles. In addition, the maintenance of computer networks and systems by professionals will allow you to do all the necessary actions more quickly than with your own hands. Although the latter option will provide valuable experience, which is not known where else it will come in handy.
Conclusion

As you can see, it's not very difficult. Of course, working with a computer is easier due to the presence of many recommendations on what and how to do, besides, it does not require manual dexterity, you just need to start the necessary processes, and the machine will do everything by itself. This is such a thing - maintenance of computer networks and systems.
Guidelines extracurricular independent work MDK 03.01 Maintenance and repair of computer systems and complexes of the Professional PM module. 03 Maintenance and repair of computer systems and complexes, specialty 230113 Computer systems and complexes
1. INTRODUCTION
The program of extracurricular independent work involves understanding and mastering such sections and topics as "Computer complex and systems", "File systems", "Operating systems", "Machine-dependent properties of operating systems", "Machine-independent properties of operating systems", "Peculiarities of work in a specific operating system (Windows)", "Peculiarities of working in a specific OS (Linux)", "Software", "Organization of maintenance of computer equipment (SVT)", "Diagnostics and troubleshooting of computer complexes and systems", "Typical fault finding algorithms.
This MDT is intended for the training of specialists of the middle technical level.
The knowledge gained during the study of this MDK is necessary when working with a computer, which in modern world is an integral part in obtaining professional education and further work of college graduates.
As a result of studying the professional module, the student must:
have practical experience:
Carrying out control, diagnostics and restoration of operability of computer systems and complexes;
Systematic maintenance of computer systems and complexes;
Debugging of hardware-software systems and complexes;
Installation, configuration and configuration of the operating system, drivers, resident programs;
be able to:
To carry out control, diagnostics and restoration of operability of computer systems and complexes;
Carry out system maintenance of computer systems and complexes;
Take part in debugging and technical testing of computer systems and complexes;
Installation, configuration and configuration of the operating system, drivers, resident programs;
Comply with the regulations of technical safety;
know:
Features of control and diagnostics of devices of hardware-software systems; basic diagnostic methods;
Hardware and software functional control and diagnostics of computer systems and complexes; possibilities and areas of application of standard and special control and measuring equipment for localization of fault points of SVT;
Application of service tools and built-in test programs;
Hardware and software configuration of computer systems and complexes;
Installation, configuration and configuration of the operating system, drivers, resident programs; techniques for ensuring stable operation of computer systems and complexes;
Pra-vi-la and norms-we oh-ra-we work-yes, tech-no-ki
security-no-sti, pro-mouse-len-noy sa-ni-ta-rii and
pro-ty-in-hot-noy for-shchi-you
The result of mastering the professional module is the mastery of the type of professional activity by students Maintenance and repair of computer systems and complexes, including professional (PC) and general (OK) competencies:
Code Name of learning outcome
PC 1To monitor, diagnose and restore the health of computer systems and complexes.
PC 2 Carry out system maintenance of computer systems and complexes.
PC 3 Take part in debugging and technical testing of computer systems and complexes; installation, software configuration.
OK 1Understand the essence and social significance his future profession show a sustained interest in it.
OK 2 Organize their own activities, determine the methods and ways of performing professional tasks, evaluate their effectiveness and quality.
OK 3 Solve problems, assess risks and make decisions in non-standard situations.
OK 4 Search, analyze and evaluate the information necessary for setting and solving professional problems, professional and personal development.
OK 5 Use information and communication technologies to improve professional activities.
OK 6 Work in a team and team, ensure its cohesion, communicate effectively with colleagues, management, consumers.
OK 7 Set goals, motivate the activities of subordinates, organize and control their work, taking responsibility for the result of completing tasks.
OK 8 Independently determine the tasks of professional and personal development, engage in self-education, consciously plan advanced training.
OK 9Be prepared to change technologies in professional activities.
OK 10 Fulfill military duty, including with the application of acquired professional knowledge (for boys).
Guidelines for extracurricular independent work are an integral part of the educational and methodological complex and are an addition to textbooks and teaching aids as part of the study MDK 03.01 Maintenance and repair of computer systems and complexes, Professional module PM. 03 Maintenance and repair of computer systems and complexes
2. LIST OF EXTRA-CURRICULUM INDEPENDENT WORK
|
Topic number |
Topic name |
Type and name of the student's work |
Number of hours to complete work |
|
Computer complex and systems |
|||
|
File systems |
Work with educational literature and notes for homework. Preparation of an essay on the topic "File systems" |
||
|
Operating Systems |
Work with educational literature and notes for homework. Preparing a message on the topic "Operating systems and environments" |
||
|
Machine-Dependent Properties of Operating Systems |
Work with educational literature and notes for homework. |
||
|
Machine independent properties of operating systems |
Work with educational literature and notes for homework. Study of additional and reference literature. |
||
|
Features of work in a specific operating system (Windows) |
Work with educational literature and notes for homework. |
||
|
Features of work in a specific OS (Linux) |
Work with educational literature and notes for homework. |
||
|
Software |
Work with educational literature and notes for homework. Preparation of an essay on the topic "Types of anti-virus programs" |
||
|
Work with educational literature and notes for homework. Study of additional and reference literature. |
|||
|
Work with educational literature and notes for homework. Study of additional and reference literature. |
|||
|
Typical algorithms for finding faults |
Work with educational literature and notes for homework. Study of additional and reference literature. |
||
|
Total |
|||
3. CONTENT OF STUDENTS' INDEPENDENT WORK EXTRA-CURRICULUM
EXTRA-CURRICULUM INDEPENDENT WORK №1
1.
Topic:Preparation of the report "Generation of microprocessors"
2.Number of hours: 9
3.Objective
4. study additional and reference literature, prepare for test tasks, write a report on the topic “Generation of microprocessors”.
Report, defense, evaluation.
EXTRA-CURRICULUM INDEPENDENT WORK №2
1.
Topic:Preparation of an essay on the topic "File systems"
2.Number of hours: 9
3.Objective: learn to select the necessary literature, isolate the main thing from it, systematize the available material.
4.General instructions for work: study additional and reference literature, prepare for a survey, write an essay on the topic “File systems”.
5. Form of reporting and control: abstract, defense, evaluation.
EXTRA-CURRICULUM INDEPENDENT WORK №3
1.
Topic:Preparing a message on the topic "Operating systems and environments"
2.Number of hours: 9
3.Objective: learn to select the necessary literature, isolate the main thing from it, systematize the available material.
4.General instructions for work: study additional and reference literature, prepare for a survey, write a message on the topic “Operating systems and environments”.
5. Form of reporting and control: message, protection, evaluation.
EXTRA-CURRICULUM INDEPENDENT WORK №4
1.
Topic:Study of additional and reference literature.
2.Number of hours: 9
3.Objective
4.General instructions for work:study additional and reference literature, prepare for the survey, abstract on the topic “ Machine-Dependent Properties of Operating Systems".
5. Form of reporting and control: synopsis, defense, evaluation.
EXTRA-CURRICULUM INDEPENDENT WORK №5
1.
Topic:Study of additional and reference literature.
2.Number of hours: 9
3.Objective: to select the necessary literature, isolate the main thing from it, systematize the available material; to deepen the knowledge, skills, students on the topic under study.
4.General instructions for work:Machine independent properties of operating systems.
5. Form of reporting and control: synopsis, defense, evaluation.
EXTRA-CURRICULUM INDEPENDENT WORK №6
1.
Topic:Preparation of a message on the topic "The concept, functions and methods of using the OS software interface"
2.Number of hours: 9
3.Objective: learn to select the necessary literature, isolate the main thing from it, systematize the available material.
4.General instructions for work: study additional and reference literature, prepare for a survey, write a message on the topic "The concept, functions and methods of using the OS programming interface."
5. Form of reporting and control: message, protection, evaluation.
EXTRA-CURRICULUM INDEPENDENT WORK №7
1.
Topic:Preparation of the report "Security in Linux"
2.Number of hours: 9
3.Objective: learn to select the necessary literature, isolate the main thing from it, systematize the available material.
4.General instructions for work: study additional and reference literature, prepare for tests, write a report on the topic "Security in Linux".
5. Form of reporting and control: report, defense, evaluation.
EXTRA-CURRICULUM INDEPENDENT WORK №8
1.
Topic:Preparation of an essay on the topic "Types of anti-virus programs"
2.Number of hours: 9
3.Objective: learn to select the necessary literature, isolate the main thing from it, systematize the available material.
4.General instructions for work: study additional and reference literature, prepare for a survey, write an essay on the topic “Types of anti-virus programs”.
5. Form of reporting and control: abstract, defense, evaluation.
EXTRA-CURRICULUM INDEPENDENT WORK №9
1.
Topic: Study of additional and reference literature.
2.Number of hours: 10
3.Objective: to select the necessary literature, isolate the main thing from it, systematize the available material; to deepen the knowledge, skills, students on the topic under study.
4.General instructions for work:study additional and reference literature, prepare for the survey, write a summary on the topic “ Organization of maintenance of computer equipment (SVT)».
5. Form of reporting and control: synopsis, defense, evaluation.
EXTRA-CURRICULUM INDEPENDENT WORK №10
1.
Topic: Study of additional and reference literature.
2.Number of hours: 9
3.Objective: to select the necessary literature, isolate the main thing from it, systematize the available material; to deepen the knowledge, skills, students on the topic under study.
4.General instructions for work:study additional and reference literature, prepare for a test task, write a summary on the topic “ Diagnostics and troubleshooting of computer complexes and systems».
5. Form of reporting and control: synopsis, defense, evaluation.
EXTRA-CURRICULUM INDEPENDENT WORK №11
1.
Topic: Study of additional and reference literature.
2.Number of hours: 9
3.Objective: to select the necessary literature, isolate the main thing from it, systematize the available material; to deepen the knowledge, skills, students on the topic under study.